Ransomware has featured prominently in the news over the last few years. Hospitals, law enforcement agencies and even individuals have been affected by it. Some have paid the ransom and recovered their computer data; others have lost their data forever. What is ransomware and how can you best protect your organization from it?
Executive Summary
OneBeacon Technology’s Joseph Budzyn explains what ransomware is and how you can protect your organization from it.It Could Happen to You
Working very late at the office on a Wednesday night trying to make a midnight deadline, Tom gets an email. He finishes the last touches on his spreadsheet and sends it off. Relieved at making his deadline and very ready to head home, Tom reads the email just before leaving.
The email is from an online company Tom has never heard of, but the message is thanking him for the order he just placed. Tom gasps; just yesterday he received a letter from his bank saying that his credit card was possibly stolen and to watch out for fraudulent charges until a new card arrives. Could this be related? The email isn’t clear, but there is an attachment with more details. Tom opens the attachment and can’t make any sense of the garbled message within. He decides to call his bank on the way home. He locks his computer and the office.
The next day, the office is in chaos. Somehow last night all of the files on the server were corrupted. No one can access any of the customer records. The IT department is not sure what happened. Tom logs onto his computer and sees a message on the screen. It says all of his files are encrypted and has instructions to buy something that will get them back. It talks about bitcoin, RSA and AES. Tom tells the IT guy that his computer is misbehaving. Thirty minutes later, with his heart pounding and fearing for his job, Tom enters the CEO’s office.
The office has become a war-room; all of senior leadership is there. IT says that Tom’s computer was infected with something called “Locky,” a type of ransomware. The ransomware has encrypted all of the files on Tom’s computer and the server. Even the backup server where all the files are regularly backed up is encrypted. They can’t get the files back. The ransom demand is for 0.5 BTC (half of a bitcoin), totaling about $350. The CEO demands, “Do we pay the ransom?”
Ransomware has affected many organizations like hospitals, universities, police departments and more. Fortunately, this story is fiction. But what is ransomware, anyway?
Ransomware is malicious software that infects a computer similar to a computer virus. A virus may destroy all of the data on the computer or use the computer to send unsolicited email. Ransomware takes the attack further by making the data inaccessible by the owner, then demanding payment before returning the data.
Ransomware has a long history, dating back to 1989 (according to Wikipedia). The particular method used to prevent access to files has varied ranging from hiding them, replacing them or encrypting them to simply lying about the files being unavailable. In early versions of ransomware, flaws in the malicious software sometimes allowed the victim to recover the files without paying the ransom. File encrypting ransomware rose to prevalence in 2013 with the rise of CryptoLocker. According to Kaspersky Lab “the number of users attacked with encryption ransomware is soaring, with 718,536 users hit between April 2015 and March 2016—an increase of 5.5 times compared to the same period in 2014-2015.”
A second type of ransomware focuses on lock access to a device. These versions pop up in a window or in some other way “lock” the computer or mobile device to prevent its usage. Sometimes the lock message will claim to be from some branch of law enforcement and accuse the user of a crime. Typically the files are not encrypted during this attack. If the lock screen ransomware is removed, the files typically remain untouched.
Ransomware initially started gaining popularity among criminals in Russia. Once it was found to be a lucrative business model, it quickly spread worldwide. Today there are readymade low-cost ransomware systems that can be purchased for $39. A would-be cyber criminal doesn’t need experience or a large investment to begin infecting computers.
Ransomware can arrive via several mechanisms. It can be in a malicious email attachment, attached to a phishing email, embedded in a malicious website download or even a web link that can automatically download the ransomware when it is clicked. Ransomware infections have even been linked to legitimate website advertisements that were poisoned in what is known as a “drive-by” infection.
Some drive-by attacks require the user to click on something. However, if the computer is missing security patches, simply loading an infected advertisement on a web page can start the infection.
Once the file-encrypting ransomware is active on a computer, it begins the process of rendering data inaccessible. Unknown to the user, the ransomware encrypts their files. If the user tries to open an encrypted file, the computer may indicate that the file is damaged. Once all of the user’s files are encrypted, the ransomware typically displays a ransom message prominently.
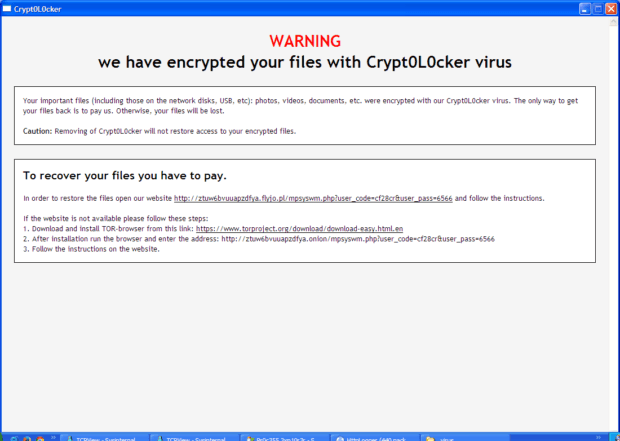
At this point the user is typically given instructions on how to pay the ransom. If the ransom is paid in a timely manner, the criminals say they will provide the user the decryption key necessary to recover their files. The payment is usually some method that is fairly convenient yet difficult to trace back to the criminals, such as wire transfers, pre-paid payment cards, premium cost SMS (text-messaging) services or a digital currency such as bitcoin.
It is important to understand that even if the ransom is paid in the timeframe required, there is no guarantee that the data will be recovered. Some versions of ransomware have flaws that make it impossible to decrypt the data. Others are simply scams where the data is encrypted and the criminals take the money but don’t deliver the decryption key. Yet other versions have “customer service” available to provide an additional means to recover the data. Criminals know if victims don’t believe they will recover their data, they will stop paying the ransom.
Paying the ransom to recover files does not prevent reinfection with the same or different ransomware and the cycle repeating. In the end, the transaction is with a criminal and the outcome is unpredictable.
Minimizing Ransomware Impact
There are preventive steps you can take to minimize the exposure and impact of a ransomware security breach.
- Maintain a current offline backup copy of important data.This backup should be disconnected from the computer and the network. Some versions of ransomware can encrypt data stored on network drives or in cloud services when they are connected to the infected computer. Don’t rely on online backups such as these; they can be encrypted as well.
- Apply vendor security patches to the operating system and to applications.Ransomware often takes advantage of software flaws to infect the computer or mobile device. Keeping up to date with security patches also protects the company from other forms of hacking.
- Use anti-virus software to detect and prevent infection.Be sure to apply security patches and signature updates to this software as well. Consider endpoint security solutions that combine features such as anti-virus, firewalls, sandboxing, web browser filtering and enterprise management for greater protection and visibility.
- Use web and email filtering software to reduce exposure to the ransomware in the first place. Train employees to be cautious about opening email attachments. Consider using a label in company email servers that indicates that an email originated outside of the company to help combat spoofing.
Be suspicious of a computer that has been infected with ransomware. Even if the data is recovered, other malicious software may be present.
Sandboxing is a computer security term referring to setting aside a program in a separate environment so that if errors or security issues occur, those issues will not spread to other areas on the computer. Programs are enabled in their own sequestered area, where they can be worked on without posing any threat to other programs.
Source: Techopedia
Even if a computer is infected with ransomware, having current offline backups available means data will still be available. As a bonus, the backup is also useful if the computer is lost, stolen or breaks.
Digital assets have become the backbone of our commercial and personal information management. Being aware of emerging risks and taking steps to protect against malicious intrusions will help mitigate your exposure to loss and downtime.
As always, the approach is a combination of people: dedicated personnel, board commitment, crisis management; policies: employee education and regular training; and technology: being proactive with software and staying ahead of the bad guy. Keep in mind that specialty insurance may help protect your bottom line.





















 Beazley Agrees to Zurich’s Sweetened £8 Billion Takeover Bid
Beazley Agrees to Zurich’s Sweetened £8 Billion Takeover Bid  Winter Storm Fern to Cost $4B to $6.7B in Insured Losses: KCC, Verisk
Winter Storm Fern to Cost $4B to $6.7B in Insured Losses: KCC, Verisk  Lessons From 25 Years Leading Accident & Health at Crum & Forster
Lessons From 25 Years Leading Accident & Health at Crum & Forster  Modern Underwriting Technology: Decisive Steps to Successful Implementation
Modern Underwriting Technology: Decisive Steps to Successful Implementation 










