The global average cost of a data breach in 2023 is $4.45 million: a 15% increase over three years, according to a recent IBM report. Additionally, the finance and insurance sector ranked as the most attacked sector from 2016 to 2020.
Insurers, agencies, and InsurTechs manage a vast amount of personal identifiable information (PII), making them prime targets for bad actors. A typical insurance organization faces an average of 113 targeted breach attempts every year. A third of those attacks will succeed.
These figures underscore the importance for insurance carriers to safeguard data and systems against theft and disruption. Protecting sensitive client data and the carrier’s reputation is a team effort, and building a strong security culture is a great way to set a precedent for current and incoming employees.
Learn more about trusted insurtech solutions by Vertafore.
Build a security-minded culture
Human error accounts for almost 40% of all data breaches.
In the recent attack on casino giants MGM Resorts International and Caesars Entertainment, a cybercriminal called a helpdesk pretending to be an employee needing a password reset, secured the information and infiltrated the casinos’ network. Even with the protection of some of the most expensive technology and rigorous operations, this attack shows how one person can jeopardize an entire organization.
A company’s security is only as good as its weakest link. Cybersecurity works best when everyone in the organization knows they are responsible for keeping data safe.
Insurance professionals are very aware of their obligations to protect PII due to insurance regulations and laws, but theory and practice can diverge dramatically. Organizations can create a security-minded culture by:
- Providing regular training on spotting common attack strategies.
- Sharing info about the latest scams that may target their personnel.
- Encouraging employees to treat all communications with a healthy skepticism so that they remain vigilant against potential attacks.
Beware of these types of cyber attacks:
Social engineering:
A manipulation technique that exploits common behavior or cultural norms to induce a victim to take an action (like clicking a link) or reveal information (such as providing their back account info).
Phishing:
An attempt to obtain sensitive data through a fraudulent email or web solicitation, where the perpetrator poses as a legitimate business or reputable person.
Spear-phishing:
A phishing attempt tailored directly to a specific individual using details unique to them.
Clone phishing:
Impersonating a well-known company or entity by cloning their official website or emails.
Smishing:
An attempt to obtain sensitive data through fraudulent texts.
Vishing:
An attempt to obtain sensitive data through fraudulent phone calls or voicemail.
Quishing:
No, we’re not making this one up. Phishing emails that use QR codes to compromise the victim’s mobile device.
Bluesnarfing:
A hacking technique to access a wireless device through a Bluetooth connection.
“For all modern businesses, consistent cybersecurity training is required to keep staff educated on the latest threats in your industry and keep everyone hyper aware of attacks that may come directly to their social media or cell phone. A good rule of thumb to follow is to never trust, and to always verify.”
– Lena Taylor, VP, Cybersecurity, Vertafore
What does cyber-risk look like for your business?
Insurance Business Magazine recently reported on the most common cyber threats hounding the insurance sector, including ransomware attacks, phishing, and simple human error that accidently exposes sensitive data.
Phishing is the most common cybercrime, with an estimated 3.4 billion malicious emails sent every day. Hackers rely on social engineering to get users to take actions—like clicking on malicious links or opening infected attachments—that expose information and systems.
Some attacks that insurance agencies see:
- Emails impersonating potential or current clients with links or attachments.
- Texts that look like they are from a coworker asking for company login information or secure access.
- Emailed invoices that look like they are from a familiar third-party vendor asking for swift payment.
Protect your company by being situationally aware. Independently verify requests and information instead of taking action from within an email. For example:
- Log directly into secure portals/sites to verify statements and make payments, rather than by clicking on an attachment or provided link.
- Before calling a phone number provided in an email, check it against known contact records or by Googling the business’s published contact information.
Suspect malicious activity? Take a screenshot or photo and report it to company leaders or the IT team. Never forward a suspicious email or text; it may inadvertently spread the attack. And as tempting as it may be to “mess” with would-be scammers, any response can put a carrier at risk.
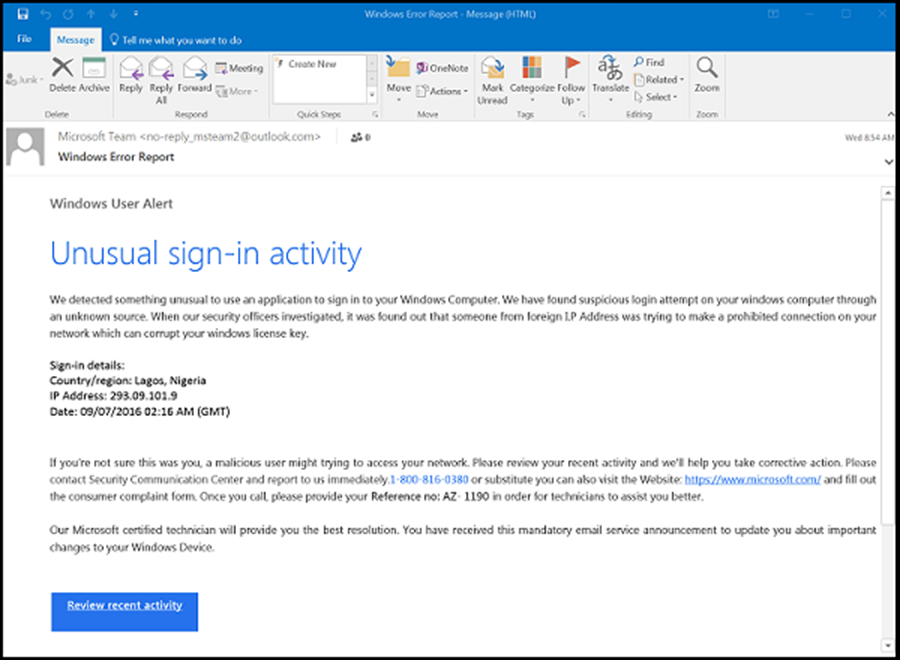
Example of a phishing email
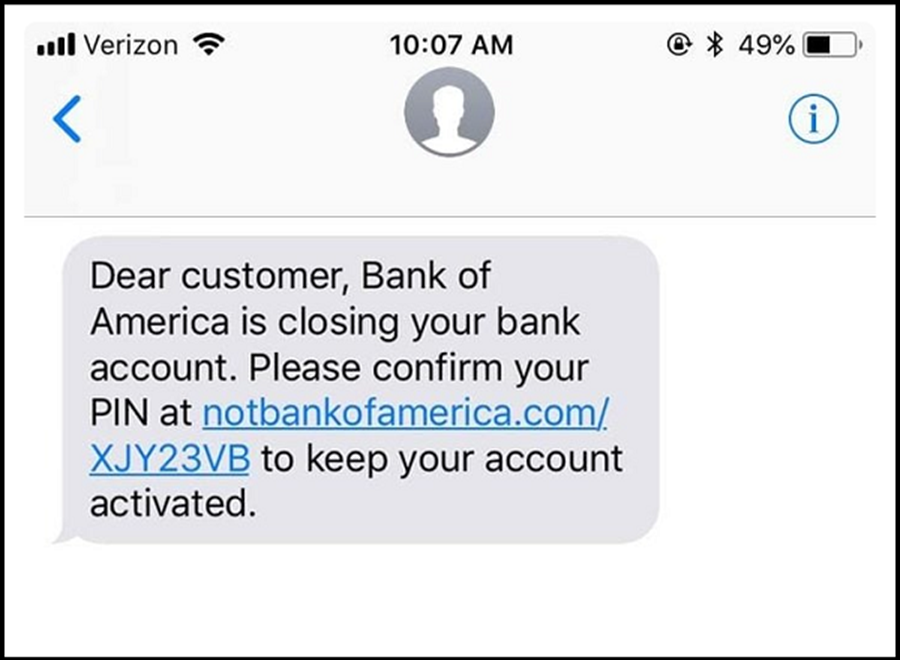
Example of smishing
“Understanding the situation by assessing the likelihood of the scenario is your best defense to ward off attackers. By using clear, frequent, and open communication with your staff, employees will be able to recognize threats, leading to a strong security culture and transparency across the organization.”
– Lena Taylor, VP, Cybersecurity, Vertafore.
Watch out for these current cybersecurity scams
A good way to spot a potential scam is to simply Google it and see what arises. A search of “Norton antivirus scam”—an email that had made the rounds this year—returns 4.3+ million hits, with top results warning consumers.
But scammers are always looking for new ways to exploit technology and changes in how people interact with information. As consumers become more wary of links in emails, one rising scam involves tampered QR codes that embed malware into the user’s phone. These codes allow criminals to gain access to the victim’s device to steal logins or access sensitive data.
Insurance professionals should also be on the lookout for a common scam through LinkedIn connection requests. LinkedIn provides would-be scammers with easy pickings for spear-phishing attacks. Scammers can reference details from a target’s profile and posts—such as a past job or recent conference attendance—to make their request seem more legitimate. Once connected, scammers may send messages with malicious links, ask for personal information to steal the victim’s identity, or even attempt to take over the victim’s LinkedIn account to impersonate them and target their network.
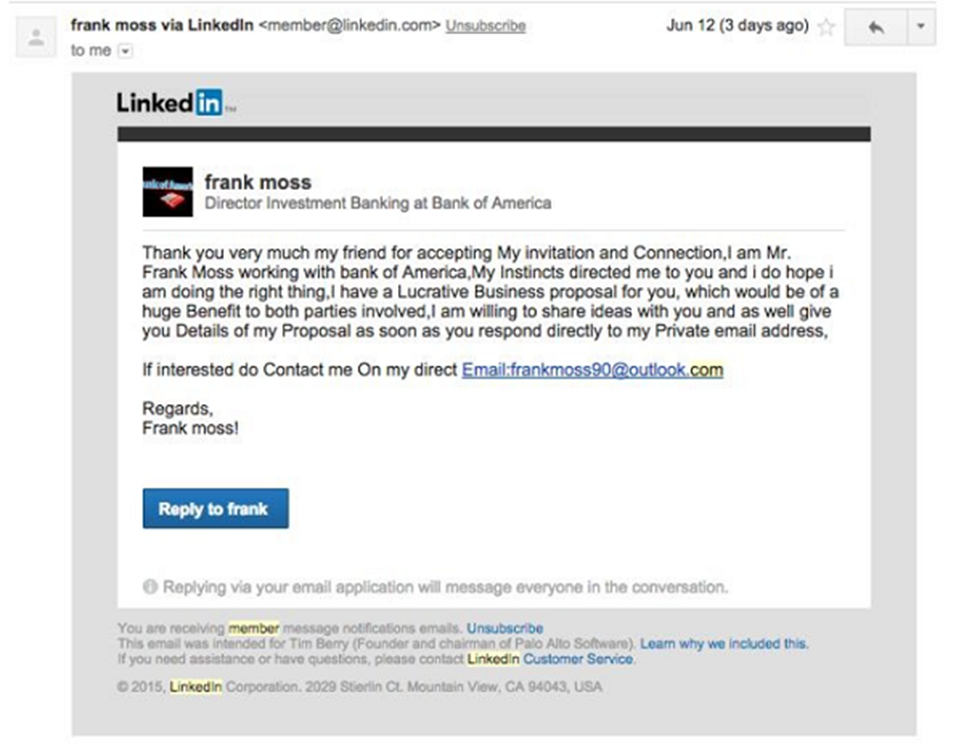
Fortunately, many of the same security precautions to combat phishing apply to these situations: always independently verify the sender, links, and request before taking any action.
The next frontier for cybersecurity and cybercriminals: Generative AI
Insurance and ChatGPT
An addition to the cybersecurity training roster this year: ChatGPT and generative AI. The insurance industry is evaluating this technology for everything from client communications to faster claims processing. But free AI tools come with a catch: the information also enters the public domain.
A free-for-all approach to generative AI tech can expose sensitive information to bad actors. For example, earlier this year, Samsung employees submitted source code and internal meeting notes to ChatGPT which led to leaked confidential company information. Mistakes like this can damage a company’s reputation and potentially lead to the loss of clients.
Generative AI platforms log every interaction and the information stays in the platform. As this technology gains in popularity and use, agencies need to clear policies on how and when their insurance professionals can use generative AI tools or solutions that are leveraging the technology.
Deepfakes are spooking cybersecurity and cyber-insurance experts
Generative AI is also spawning a new avenue for criminals: the ability to create media—especially images, videos, and audio files—that convincingly impersonate real people or create “evidence” of events that never happened.
These deepfakes can be used by bad actors in multiple ways. A scammer can create a deepfake of a person’s voice or likeness to trick business associates or family into sharing confidential information, handing over cash, or providing access to sensitive systems. In one high-profile case, a bank manager transferred millions of dollars to fraudsters after talking on the phone to his “director.”
The problem with deepfakes is that they can be highly effective—and they are likely to become more so as AI technology perfects the ability to clone human speech and likenesses.
CEOs and other high-profile individuals at an organization are highly susceptible to deepfakes because their likeness and voice is often readily available. Pictures, interviews, and recorded presentations can be used to create a deepfake that “shows” the executive behaving badly or saying some offensive. When the image spreads across social media, it can cause a flurry of bad publicity that impacts sales and revenue.
That’s why some cyber-insurance policies are now covering corporate damages from deepfakes. But these policies may also require clients to implement deepfake detection software, and to monitor the web for deepfakes related to their business.
Learn more about trusted insurtech solutions by Vertafore.
Time to talk to your agents and end-insureds about cybersecurity
Cybersecurity Awareness Month is a great time to talk to your appointed agents and insureds about minimizing their risk from current scams and malicious activity. Keep up-to-date on the Federal Trade Commission’s cybersecurity toolkit and make sure to have a plan in place in case a breach does happen.
Some time and tips include:
- Never send sensitive personal or financial information through email.
- Don’t open email attachments unless you trust the source.
- Don’t follow links in an email asking for sensitive personal or account information, even if the source looks familiar.
- Ask questions. If you’re suspicious, call the company that the email appears to be from, and ask about the message.
- Pause before you response to emails, texts, or calls that ask for personal information
The bottom-line
By implementing a security-minded culture and staying vigilant against malicious attacks, your company can significantly reduce the risk of a breach taking place and be better equipped to respond effectively if one ever occurs.




















 20,000 AI Users at Travelers Prep for Innovation 2.0; Claims Call Centers Cut
20,000 AI Users at Travelers Prep for Innovation 2.0; Claims Call Centers Cut  AIG, Chubb Can’t Use ‘Bump-Up’ Provision in D&O Policy to Avoid Coverage
AIG, Chubb Can’t Use ‘Bump-Up’ Provision in D&O Policy to Avoid Coverage  Earnings Wrap: With AI-First Mindset, ‘Sky Is the Limit’ at The Hartford
Earnings Wrap: With AI-First Mindset, ‘Sky Is the Limit’ at The Hartford  Retired NASCAR Driver Greg Biffle Wasn’t Piloting Plane Before Deadly Crash
Retired NASCAR Driver Greg Biffle Wasn’t Piloting Plane Before Deadly Crash 