A substantial disruption in the U.S healthcare system occurred as a result of a February cyber attack on Change Healthcare (CHC), a subsidiary of UnitedHealth Group.
Change Healthcare, a medical data clearinghouse, provides data to insurance companies to facilitate payment of claims and prescriptions.
On February 21, Change Healthcare experienced a ransomware attack where patient data and encrypted files were stolen.
To mitigate the damage, CHC brought most of its services offline. This created a ripple effect felt throughout the entire U.S. healthcare system.
According to a March newsletter by cyber broker Coalition, Inc., the attack was conducted by ALPHV/BlackCat, the same group responsible for the MGM Resorts disruption last year.
“This group is known for its double-extortion tactics, involving the theft of sensitive data followed by encrypting files and demanding ransom for both decryption and the non-release of the stolen data,” Coalition, Inc. stated in its newsletter.
Four terabytes of data, including Social Security numbers, healthcare records and company source code, were claimed to have been stolen.
The disruption caused by the cyberattack highlights weaknesses within the healthcare system and other critical infrastructures using Single Point of Failure (SPoF) technology, according to a recent CyberCube blog written by William Altman, cyber threat intelligence principal, Ethan Spangler, PhD and lead economist, and Jon Laux, VP of Analytics.
Single point of failure means that there is a flaw in a system of technology that can give way to a hard stop in its function if a malfunction occurs. Obviously, if critical infrastructures rely on SPoF technology, there is a substantial vulnerability to the public.
According to CyberCube, CHC provides software for clinical services used by medical providers and “runs a membership platform for patient services, giving it access to tens of millions of patient records.”
CHC completes 15 billion healthcare transactions annually, according to its website.
The cyberattack has led to payment delays for patient services and healthcare, as well as delays in compliance and regulatory reporting.
Because of cash flow problems that have resulted from the attack, providers are seeking funds to stay afloat.
UnitedHealth Group indicates it is mitigating the impact on consumers and care providers by funding more than $3 billion to care providers through a Temporary Funding Assistance program.
The insurer has established a timeline for restoring services, with an estimation that all services will be restored by the end of April.
“We are committed to providing relief for people affected by this malicious attack on the U.S. health system,” said Andrew Witty, CEO of UnitedHealth Group in a March 7, 2024, statement. “All of us at UnitedHealth Group feel a deep sense of responsibility for recovery and are working tirelessly to ensure that providers can care for their patients and run their practices, and that patients can get their medications. We’re determined to make this right as fast as possible.”
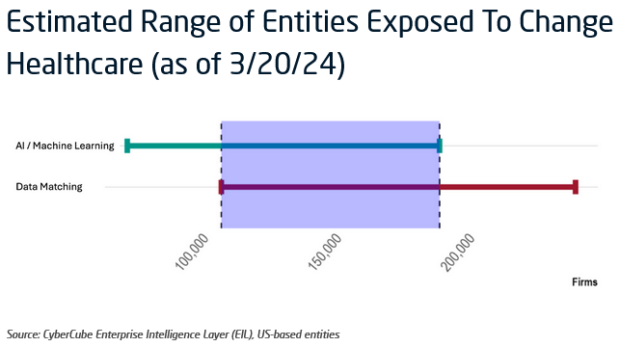
To provide cyber insurers and reinsurers a better grasp of the exposure in this cyber event, CyberCube estimated the number of entities exposed to be between 107,000 to 189,000, based on a combination of Artificial Intelligence and Data Matching analysis of SPoF data (as of March 20, 2024).
“The estimate is indicative of the number of entities potentially exposed, and not necessarily the number of claims or financial losses that could be experienced from this event remains a high degree of uncertainty as to the total costs related to this event as CHC begins to bring services back online,” the authors noted.
Data privacy and reputational damage are major concerns related to the hack, according to Coalition Inc.
The CyberCube authors recommend that cyber insurers and reinsurers continue to monitor reports relating to personal health information (PHI) stolen in the attack.
One area of cyber insurance that is often overlooked, according to Coalition Inc., is contingent business interruption coverage. Currently, most of what the cyber broker is seeing is a disruption of third-party vendors. “All of the claims we’ve seen among Coalition policyholders relate to the risk that a third-party provider will be breached,” Coalition said in its newsletter.
The cyber broker is also taking this time to discuss security technology currently used by its clients.
Recognizing the interconnectedness of the U.S. healthcare system, the government has said it is focusing on steps to increase cyber resilience in the healthcare system.




















 Berkshire-owned Utility Urges Oregon Appeals Court to Limit Wildfire Damages
Berkshire-owned Utility Urges Oregon Appeals Court to Limit Wildfire Damages  Flood Risk Misconceptions Drive Underinsurance: Chubb
Flood Risk Misconceptions Drive Underinsurance: Chubb  Execs, Risk Experts on Edge: Geopolitical Risks Top ‘Turbulent’ Outlook
Execs, Risk Experts on Edge: Geopolitical Risks Top ‘Turbulent’ Outlook  Nearly 26.2M Workers Are Expected to Miss Work on Super Bowl Monday
Nearly 26.2M Workers Are Expected to Miss Work on Super Bowl Monday 




