Late last week, federal lawmakers requested information from Chicago-based insurer CNA about a March 21 cyber attack on the company and about a reported $40 million ransom CNA paid to end the incident.
In a letter of CNA’s chief executive officer, Dino Robusto, Rep. Carolyn Maloney, D-N.Y., who chairs the Oversight and Reform Committee of the U.S. House of Representatives, also expressed fears about the pattern that is developing when companies like CNA and Colonial Pipeline agree to pay attackers to get their systems restored.
“I am concerned that the decision to pay the cybercriminal actors sets a dangerous precedent that will put an even bigger target on the backs of companies at risk for ransomware attacks going forward,” Rep. Maloney wrote in a letter just days after news also emerged that a major meatpacker had suffered a cyber attack and a day before NBC News reported that two local TV stations (one NBC affiliate and an ABC affiliate) were forced offline because of possible cyber attacks. “CNA’s payment of a ransom to cybercriminals is the latest example of a company paying millions of dollars in ransom without any public disclosure,” Rep. Maloney said.
She also sent a letter to the leader of Colonial Pipeline, CEO Joseph Blount, expressing similar concerns in almost the same words. But while Blount confirmed the $4.4 million payment made to get the pipeline operating to the Wall Street Journal (May 19, 2021), the Congresswoman noted that media reports about CNA only cited unnamed sources reporting a ransom amount that was nearly 10-times bigger, without the CEO’s confirmation of the payout.
During a May 1 earnings conference call, Robusto did confirm that CNA had “sustained a sophisticated cybersecurity attack” caused by ransomware in late March, causing the insurer to proactively disconnect systems from its network to contain the attack and to ensure that external parties were not at risk of cross contamination. Agents and brokers were kept in the loop on developments as they unfolded during a three-week restoration process, he said, adding that operations are now back to normal and that no evidence was unearthed to indicate that external customers were at risk of infection or cross-contamination due to the incident.
Robusto did not mention the ransom payment during his conference call remarks. CNA also did not confirm the ransom payment in response to a question from Carrier Management on Friday but did confirm receipt of the letter from Rep. Maloney. “CNA is currently reviewing the letter and will respond appropriately,” the company said in a statement. “While our investigation is still ongoing, CNA is confident that the attack has been successfully contained and we are operating normally. We support Congress in their efforts to understand and identify appropriate solutions to the growing threat of ransomware attacks.”
Notably, Maloney’s letter does not just request “documents and communications” relating to the attack and to the ransom payment. It also requests information on claims incurred by CNA to cover cyber risks, without clarifying whether those claims necessarily had to arise under standalone cyber insurance policies. Specifically the letter asks for documents “sufficient to show, in fiscal years 2020 and 2021…the aggregate number of claims relating to a ransomware attack, data breach incident, or other information security incident by holders of insurance policies issued or brokered by CNA or its affiliates,” along with the aggregate total dollar amount paid on those claims and the highest dollar amount paid on any single claim.
In early May, Paris-based AXA announced that it would stop writing cyber insurance policies that reimburse policyholders for extortion payments made to cyber attackers but CNA and other global insurers have not made any similar announcements—and AXA’s action is confined to France only.
“Congress needs detailed information about ransom payments that companies like CNA made to cybercriminal actors to legislate effectively on ransomware and cybersecurity in the United States,” Rep. Maloney’s letter to CNA said, prefacing the request for information and documents, “regardless of whether they reside on personal or business systems or accounts” by June 17, 2021.
Separately, the General Accountability Office (GAO) sent a letter to Congress last month accompanying a new report on the cyber insurance market revealing that the GAO would be issuing a report later this year on the costs and insurance for cyber terrorism, including the extent to which the federal Terrorism Risk Insurance Program is able to respond to cyber attacks and cyber terrorism.
Rep. Maloney, who led efforts to extend the Terrorism Risk Insurance Act authorizing TRIP over the years, also introduced a proposed Pandemic Risk Insurance Act, a federal reinsurance backstop for pandemic-related business interruption insurance risk last year, modeling the proposal after TRIA.
Where CNA Ranks Among Cyber Insurers
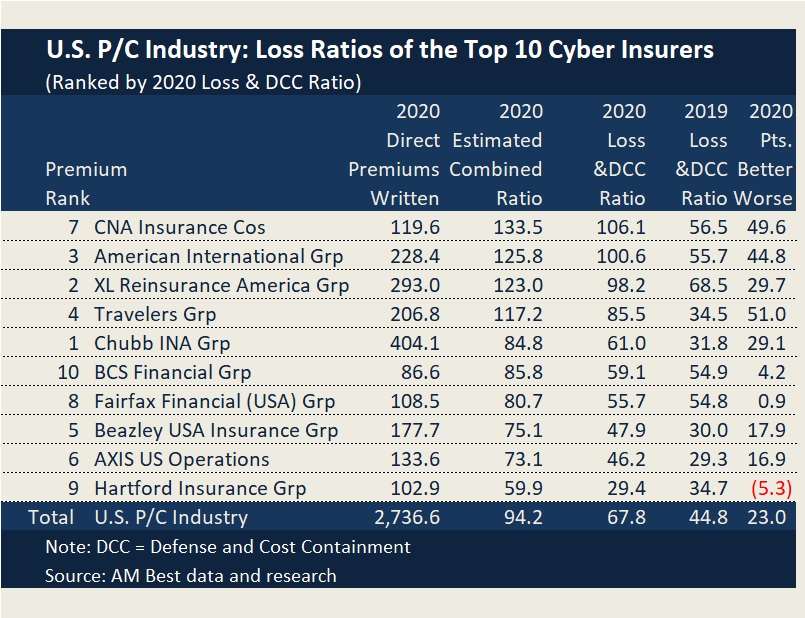
A report published by AM Best late last week lists CNA as the seventh largest writer of cyber insurance in a ranking based on 2020 direct written premiums or and sixth largest based on 2020 policies in force. (See related article, “Time For P/C Insurers To Totally Reassess ‘Grim’ Cyber Insurance Market: AM Best,” for premium ranking and AM Best’s analysis of market trends.)
The premium data indicate that nearly 85 percent of the policies written by CNA last year were packaged polices rather than standalone cyber policies.
According to the AM Best report, larger entities tend to purchase standalone coverage and manage their cyber risks explicitly while small and medium-sized enterprises may be satisfied with cyber coverage as part of a package.
For the industry overall, standalone policies accounted for about 60 percent of 2020 direct written premiums premium, but packaged policies accounted for about 95 percent of policies in force, AM Best reported.
On the loss side, CNA’s loss and defense cost ratio was the worst among the top 10 writers in 2020 at 106.1, contributing to an estimated combined ratios of 133.5 based on AM Best’s analysis of NAIC supplement data. Among the top 20 writers, only Sompo Holdings was worse, with a loss and DCC ratio of 114.1 and an estimated combined ratio of 136.4.
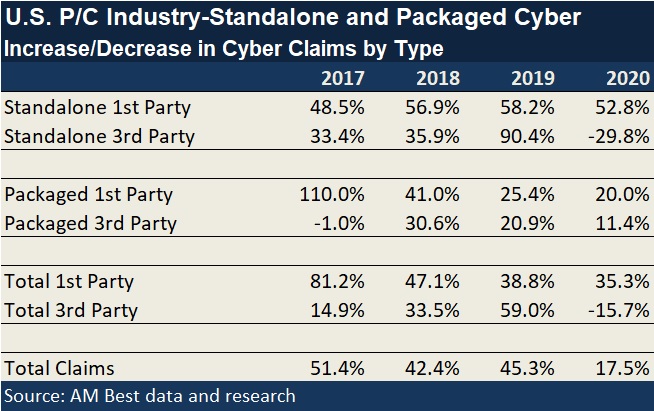
Overall, the industry loss and defense cost ratio jumped 23 points to 67.8 in 2020, AM Best reported. AM Best also analyzed changes in the number of first-party cyber claims and third-party claims for each of the last five years, attributing the first-party claims to ransomware. That analysis reveals that in 2020 the first-party ransomware claims (incurred under standalone and package policies combined), jumped 35 percent in 2020. On average, first-party claims soared almost 50 percent per year over the years 2016-2020.
Although first-party claims represented the majority of claims in each of the five years, in 2020, first-party claims represented 75 percent of the total, up from just 55 percent in 2016.
Third-party claims rose roughly 20 percent per year over the same five-year time period, but actually fell nearly 16 percent in 2020.





















 Focus on Ski Guides After Deadly California Avalanche Could Lead to Criminal Charges, Civil Suits
Focus on Ski Guides After Deadly California Avalanche Could Lead to Criminal Charges, Civil Suits  From Skill to System: The Next Chapter in Insurance Claims Negotiation
From Skill to System: The Next Chapter in Insurance Claims Negotiation  The Future of HR Is AI
The Future of HR Is AI  Is Risk the Main Ingredient in Ultra-Processed Food?
Is Risk the Main Ingredient in Ultra-Processed Food? 














